Threatsift
Overview

Integrated Hybrid Cloud Management Platform
Threatsift 플랫폼
SIEM concentrates mainly on log-based information-collection, detection, alert through deployed appliances,
and are inadequate to correlate the incidents due to the absence of threat resources and attack history management.
In short, separated/alienated analysis and response lead to discrepancy between detection, analysis, response and management.
Threatsift
Features
I am text block. Click edit button to change this text.
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Auto-analysis
-
Auto-extraction
-
Intellect profiling
-
Integrated solution
-I am text block. Click edit button to change this text.
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Threatsift
Architecture
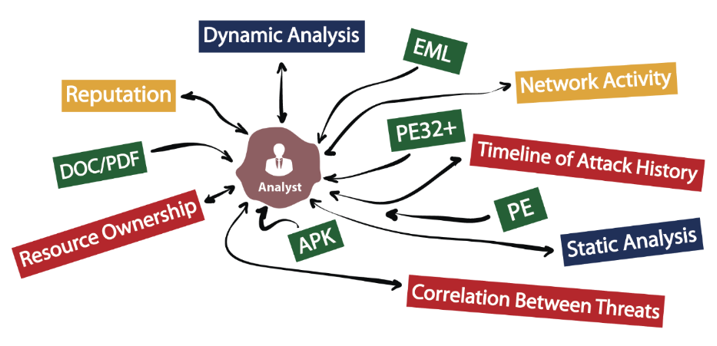
Chaos of Analyst
- Fragmented Information Management
- Unextractable Linkage Information
- Ineffective Response Planning
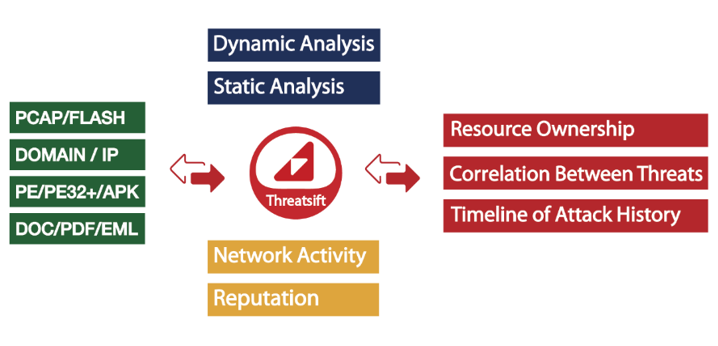
Harmony of Cyber Investigation
- Comprehensive Information Management
- Extractable Static/Dynamic Analysis
- Effective Response Planning
Threatsift
Specification
| 구분 | 상세 | ||
|---|---|---|---|
| 1 |
|
||
| 2 |
|
||
| 3 |
|
||
| 4 |
|
||
Threatsift
Product Video
Auto-extraction
Auto-extraction
Automated-extraction of information on each threat resource
Auto-extraction
Auto-extraction
Automated-extraction of information on each threat resource
Auto-extraction
Auto-extraction
Automated-extraction of information on each threat resource
Auto-extraction
Auto-extraction
Automated-extraction of information on each threat resource
Definition for Threat Normalization
Threat Normalization [θret nɔ́:rməlizéiʃən]
Process of optimization for unified storage & analysis to meet the requirements to secure the process management quality(real-time, accuracy, efficiency, etc.) on various and atypical threat information(malware, network resources, communication channels, reputation Information, threat level, etc.) collected for decisive threat response.
The Power of Threat Normalization
Without Threat Normalization
- Unclear Criterion of Integrated Information
- Absence of Association Key
- Inevitable Manual Collection
With Threat Normalization
- Definite Criterion of Integrated Information
- Existence of Association Key
- Manual Collection Eliminated
The Type of Threat Normalization
- Domain : Ownership / DNS Records / Malicious History
- IP : ISP / Class Info / Malicious History / Base10
- Binary(PE/APK) : HASH / API Sequence / C2 Connection
- EML : Session / Body / Attachment
- Event Log : Timestamp(UTC) / Schema / Value Type
- Collection Channel : Resolution / Rotation / Reliability
- Threat Level / Whitelist / Blacklist / Reputations
- Malicious Activity Categorization